Week 5 of my CodePath's Intermediate Cybersecurity course!
Security Information & Event Management (SIEM)
SIEM tools use rules and statistical correlations to turn log entries and events from security systems into actionable information.
- Detect threats in real time
- Manage incident response
- Forensic investigation on past security incidents
- Prepare audits for compliance purposes
SIEM combines 2 functions:
- SIM — security information management.
- SEM — security event management.
→ Makes SIEM more well-rounded and an ubiquitous tool for any Security Operation Center (SOC).
Some SIEM tools include: Splunk Enterprise Security, Datadog Security Monitoring, Fortinet FortiSIEM, etc.
In short, SIEM is a solution that helps organizations detect, analyze, and respond to security threats before they harm business operations. — Microsoft
Next-gen SIEM capabilitites
Next-gen SIEM utilizes User and entity behavior analytics (UEBA) to go beyond rules and correlations, leveraging AI and deep learning techniques to look at patterns of human behavior.
-
Security orchestration and automation response (SOAR): Next-gen SIEMs integrate with enterprise systems and automate incident response. Eg: SIEM detects an alert for ransomware → SIEM performs containment steps automatically on affected systems before attackers encrypt the data → simultaneously creating communications or other notifications.
-
Complex threat identification: Correlation rules can’t capture many complex attacks, because they lack context, or can’t respond to new types of incidents. With automatic behavioral profiling, SIEMs detect behavior that suggests a threat.
-
Detection without rules or signatures: Many threats can’t be captured with manually-defined rules or known attack signatures. SIEMs use machine learning to detect incidents without pre-existing definitions.
-
Lateral movement: SIEMs analyze data from across the network and multiple system resources to detect lateral movements — attackers move across network, IP addresses, etc.
-
Entity behavior analysis: Critical assets on the network — servers, medical equipments, etc. — have unique behavioral patterns. SIEMs learn these patterns and automatically discover anomalies suggesting a threat.
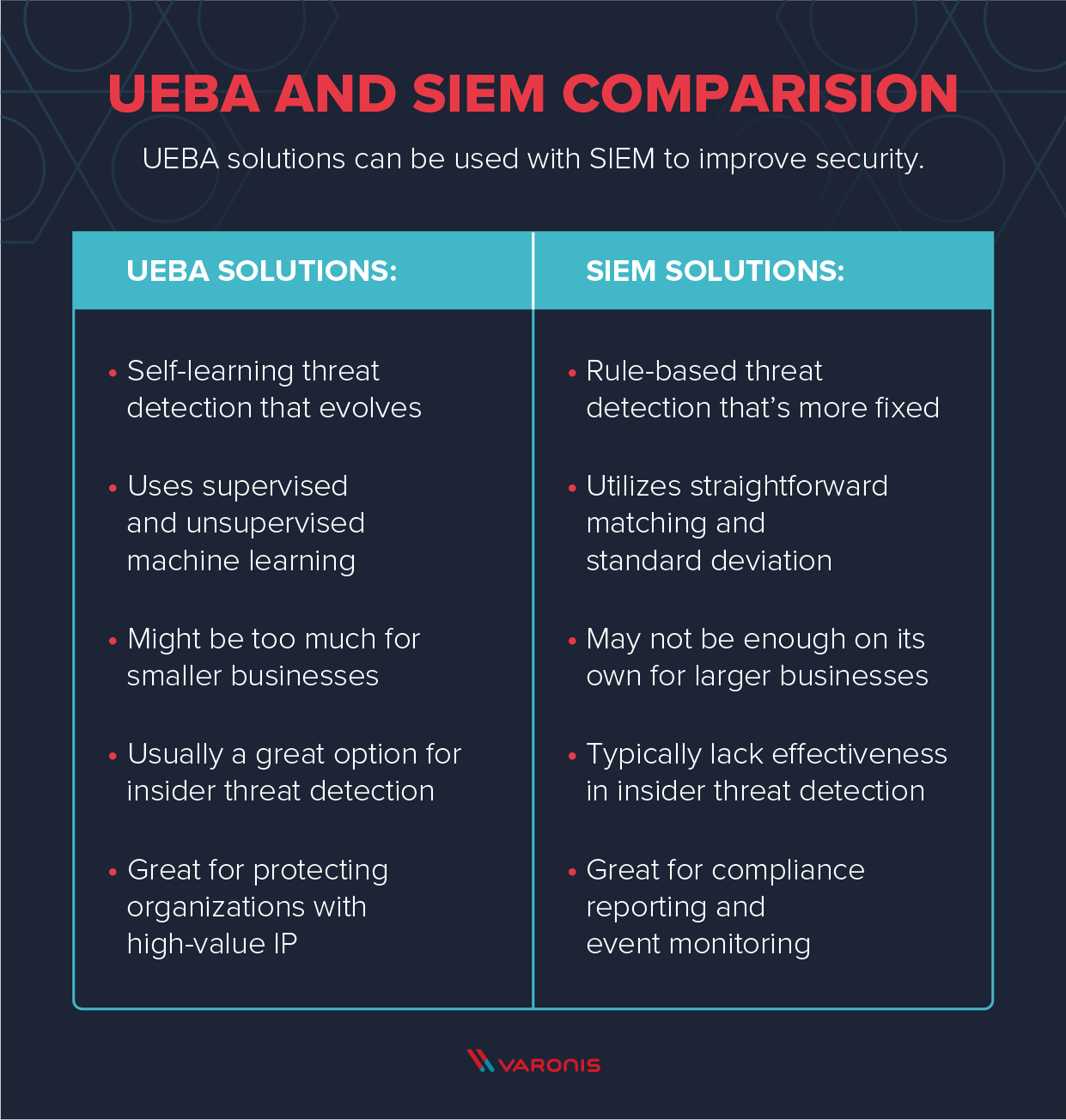
User and entity behavior analytics (UEBA)
UEBA provides information on the behavior of users and other entities in the corporate network — malicious insider, compromised user, etc.
3 pillars of UEBA
Analytics: detects anomalies using a variety of analytics approaches — machine learning, statistical modeling, etc.
Data sources: ingest data from a general data repository such as a data lake or data warehouse, or through a SIEM. Can be from:
- Business context
- HR and user context
- External threat intelligence
- Events and logs
- Network flows and packets
Insider threats
Negligent insider: An employee with privileged access to IT systems unintentionally puts their org at risk because they don’t follow the procedures.
Malicious Insider: employee intends to perform a cyber attack against the org.
Compromised insider: infiltrate an org and compromise a privileged user account.
Source: Varonis